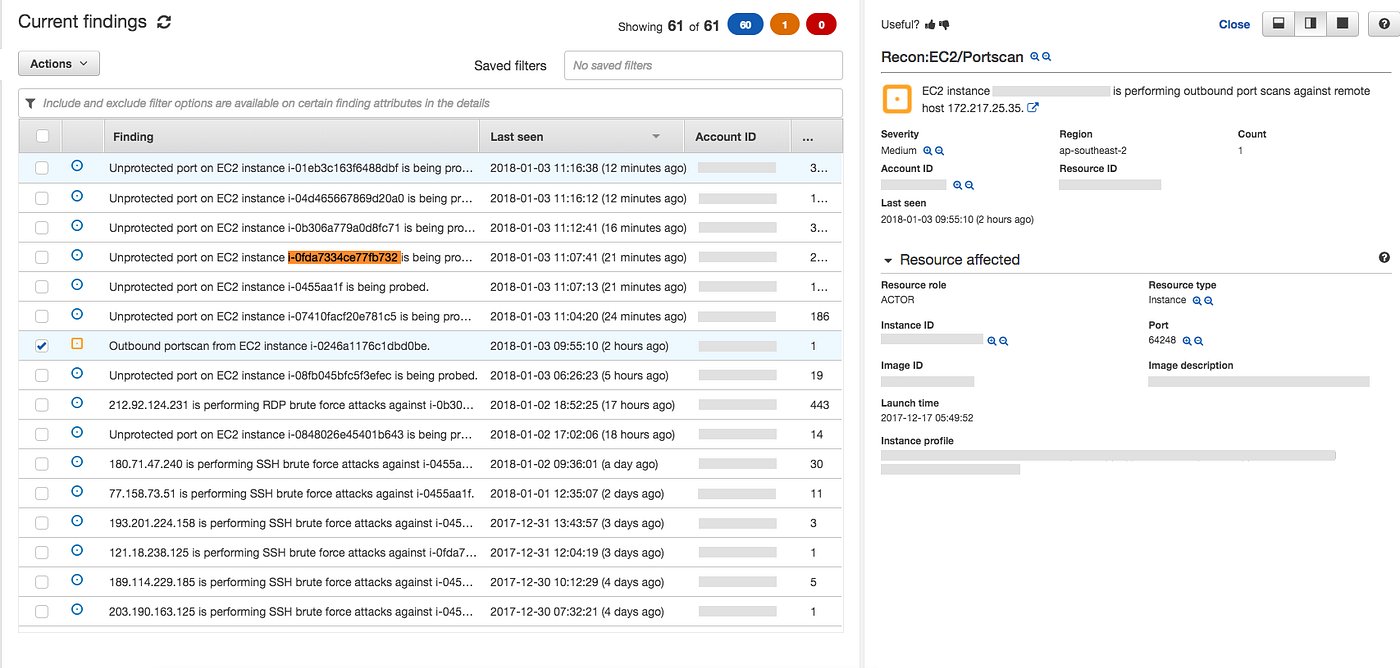
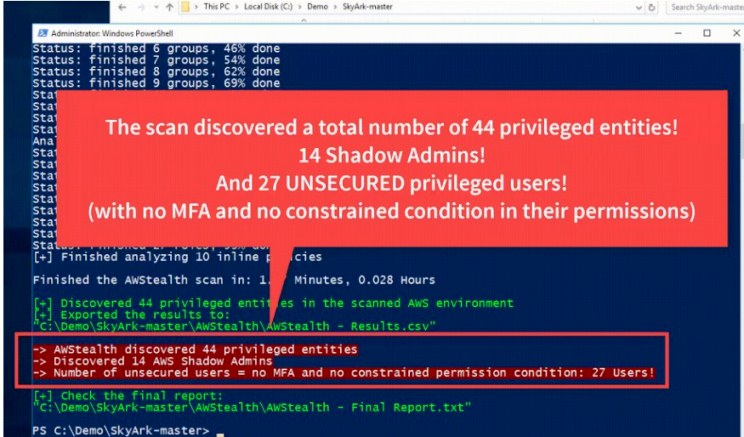
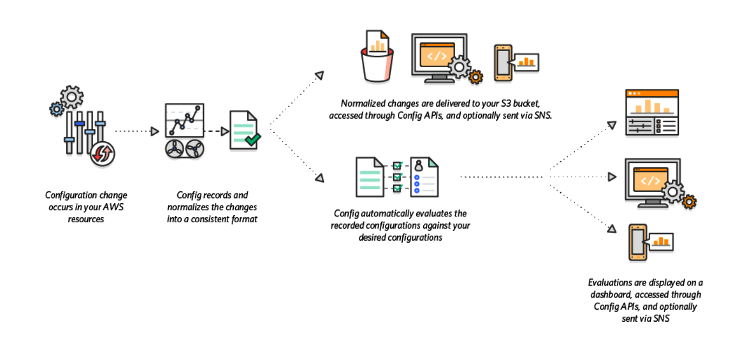
Amazon S3 Malware Scanning Using Trend Micro Cloud One and AWS Security Hub | AWS Partner Network (APN) Blog

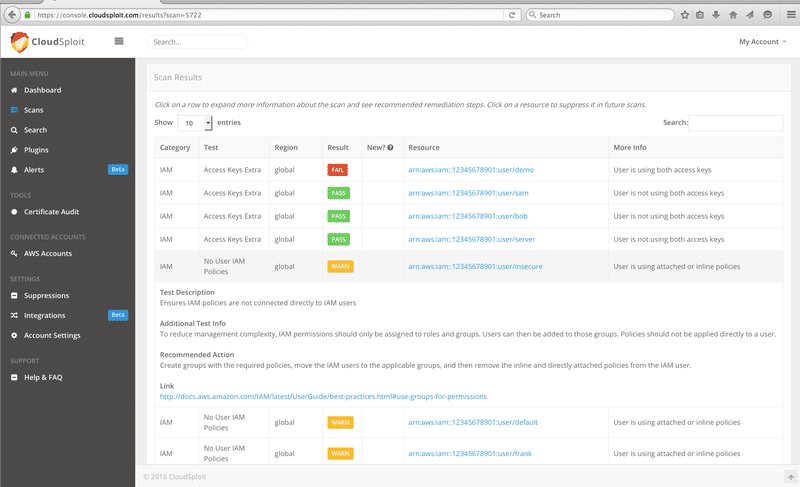
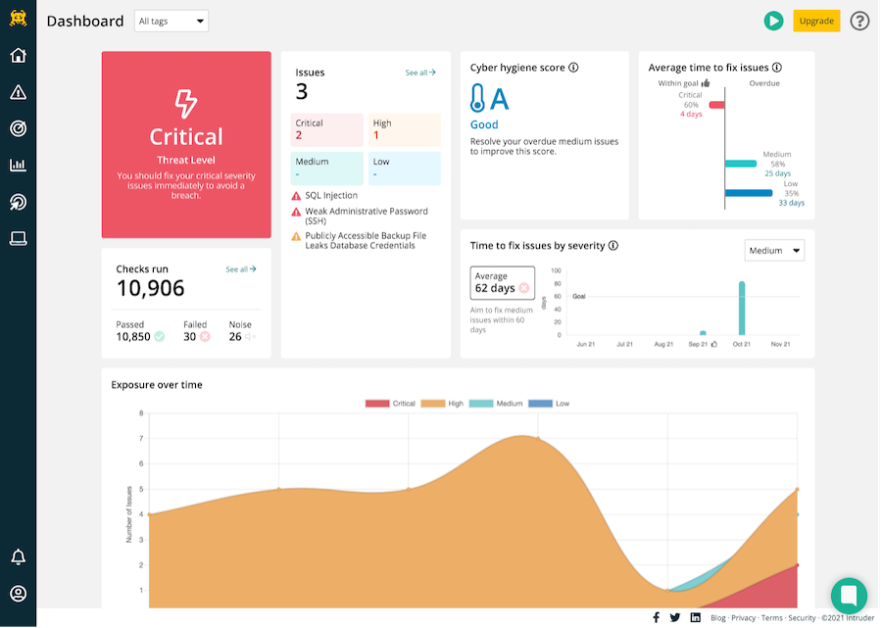
Top Security Scanning and Vulnerability Management Tools |AWS| | by Kubernetes Advocate | AVM Consulting Blog | Medium

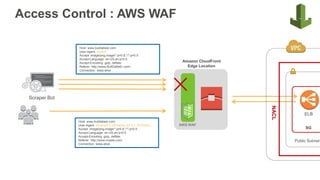
Using AWS security services to protect against, detect, and respond to the Log4j vulnerability | AWS Security Blog

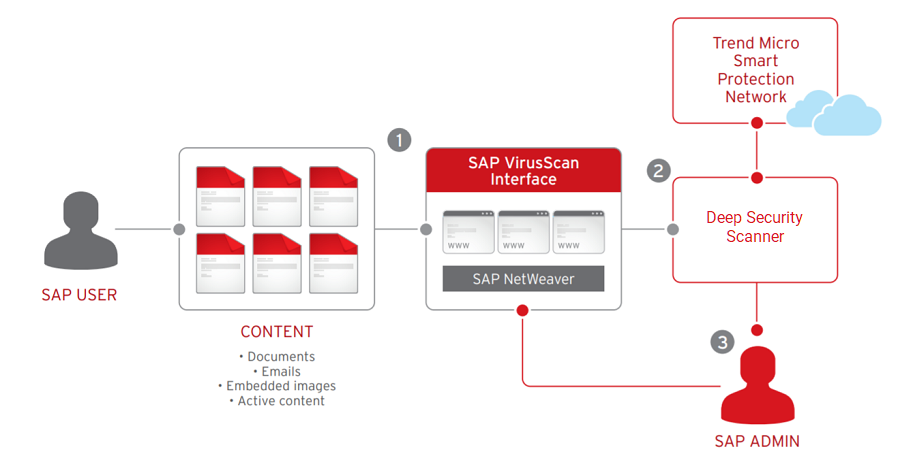
Amazon S3 Malware Scanning Using Trend Micro Cloud One and AWS Security Hub | AWS Partner Network (APN) Blog

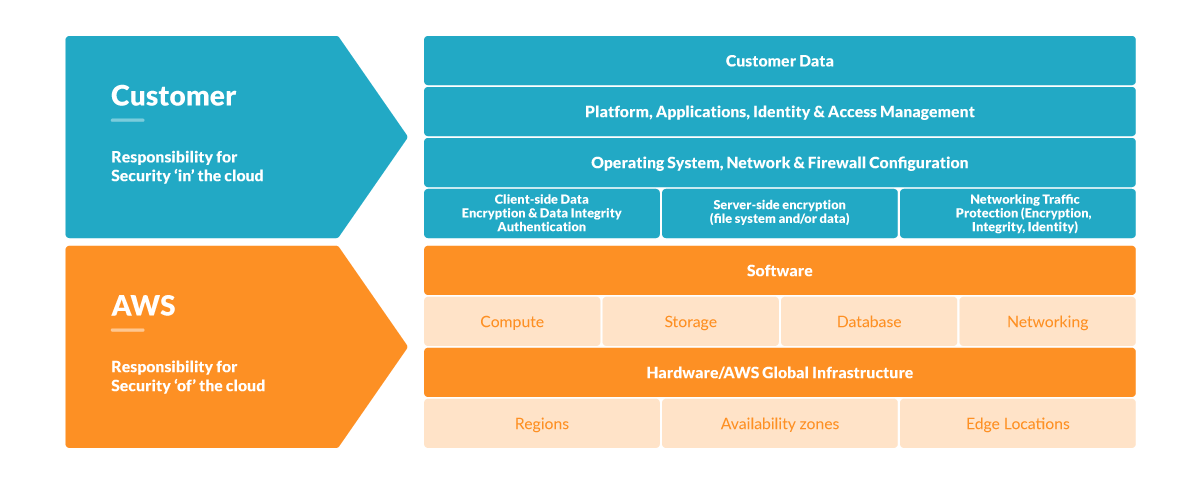
Amazon S3 Malware Scanning Using Trend Micro Cloud One and AWS Security Hub | AWS Partner Network (APN) Blog

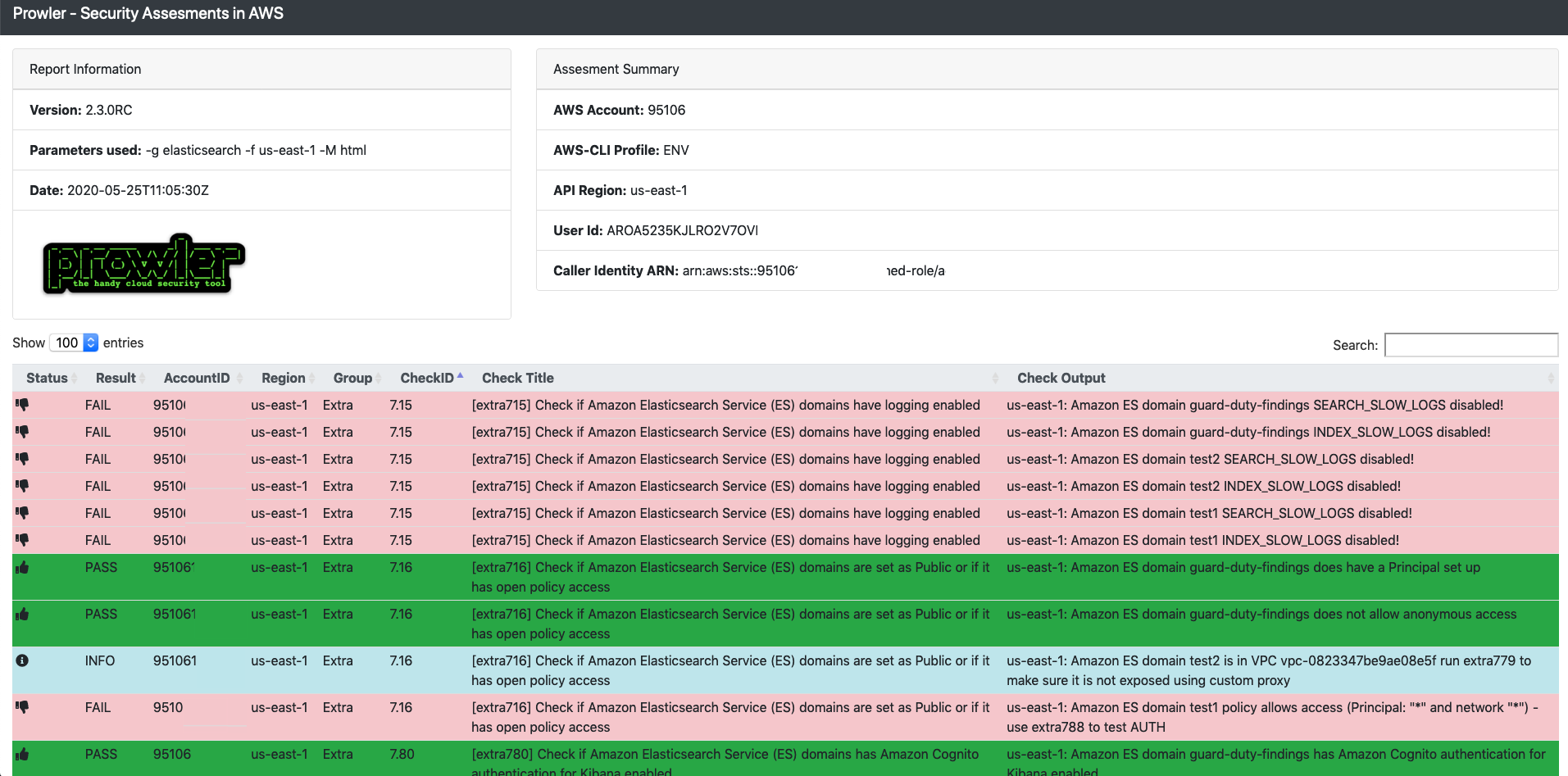
Amazon S3 Malware Scanning Using Trend Micro Cloud One and AWS Security Hub | AWS Partner Network (APN) Blog

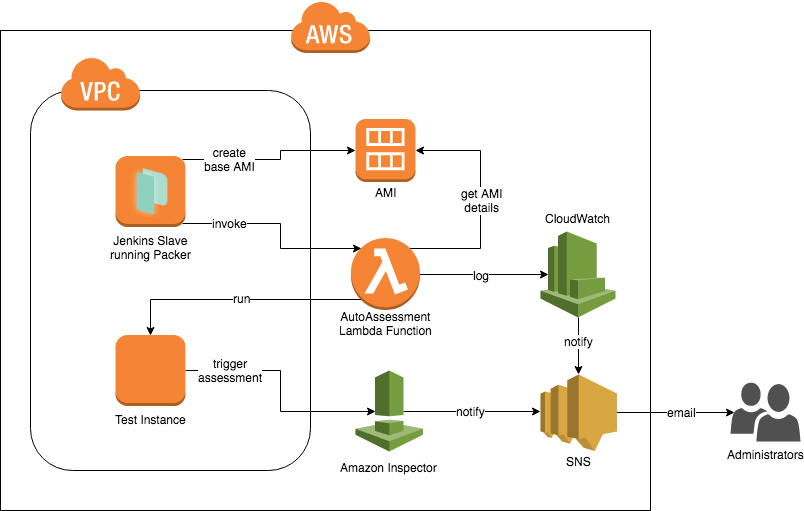
How to Set Up Continuous Golden AMI Vulnerability Assessments with Amazon Inspector | AWS Security Blog

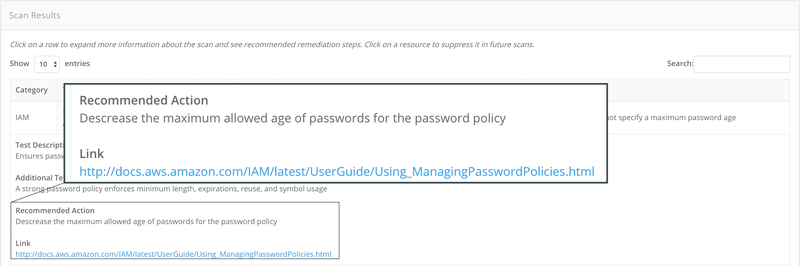
Amazon S3 Malware Scanning Using Trend Micro Cloud One and AWS Security Hub | AWS Partner Network (APN) Blog
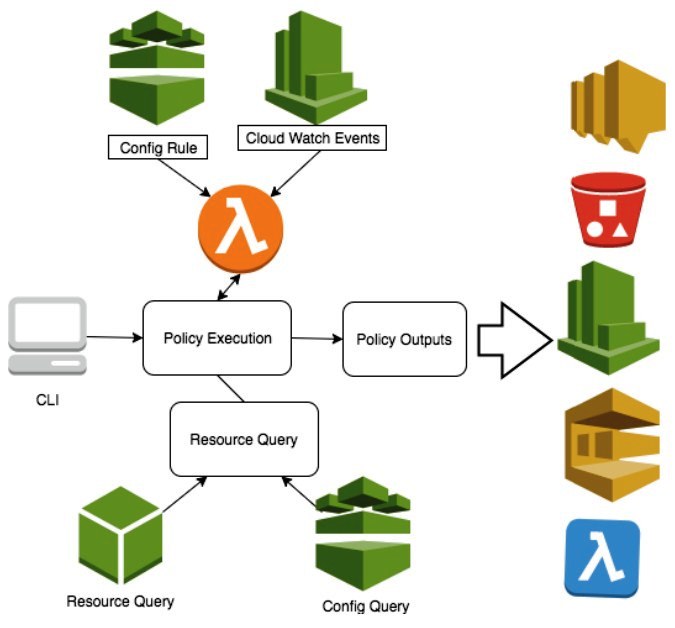
GitHub - future-architect/vuls: Agent-less vulnerability scanner for Linux, FreeBSD, Container, WordPress, Programming language libraries, Network devices